Table of Content
Try Vizitor for Free!

Tue, Mar 25, 2025
Read in 12 minutes
Did you know? Businesses that don’t use Visitor Management Systems (VMS) face many problems. For example, in a busy office where visitors come for meetings or interviews, things can get chaotic without a proper system. Imagine losing visitor information, letting people into restricted areas by mistake, or needing stronger security. These issues mess up daily work and put important data and safety at risk.
A good Visitor Management System can make a big difference for your business. First, it makes things safer by keeping accurate records of visitors and giving them special access cards, so only the right people get into certain places. Second, it makes things faster and smoother by automating check-ins, cutting down wait times, and making visitors’ experience better. Third, it lets you keep an eye on what visitors are doing in real time, so you can act fast if something goes wrong.
In short, a good Visitor Management System isn’t just a helpful tool—it’s a smart investment that protects your business, makes it run better, and shows you’re serious about professionalism. To learn more about why a digital visitor management system is so important and how it can improve your business, check out our detailed blog below.
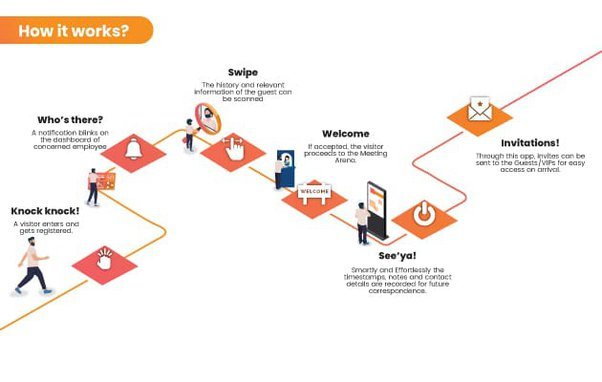
How Has Visitor Management System Changed The Entire Business World?

The use of Visitor Management Systems (VMS) has brought significant changes to the business world:
1. Enhanced Security
VMS has revolutionized how businesses approach security. By accurately tracking and managing visitor access, companies can prevent unauthorized entry, reduce security breaches, and safeguard sensitive information.
2. Improved Efficiency
With automated check-in processes and streamlined visitor registration, VMS has boosted operational efficiency. This saves time for both visitors and employees, leading to smoother workflows and enhanced productivity.
3. Better Visitor Experience
VMS has transformed the visitor experience by eliminating long wait times, simplifying check-in procedures, and providing a more personalized welcome. This improves customer satisfaction and leaves a positive impression.
4. Real-Time Monitoring
Modern VMS solutions offer real-time monitoring of visitor activities, allowing businesses to respond promptly to any security incidents or emergencies. This proactive approach enhances overall safety and risk management.
5. Data Insights
VMS generates valuable data insights about visitor patterns, peak hours, and frequently visited areas. This data can inform decision-making, optimize resource allocation, and improve facility management strategies.
6. Regulatory Compliance
Many industries have strict regulatory requirements for visitor tracking and access control. VMS helps businesses stay compliant with regulations, reducing legal risks and ensuring a secure environment for all stakeholders.
7. Integration With Other Systems
VMS can integrate seamlessly with other business systems such as access control, CRM software, and employee databases. This integration enhances data accuracy, facilitates information sharing, and creates a more cohesive operational ecosystem.
Features Of Visitor Management System
Visitor Management Systems (VMS) typically offer a range of features designed to streamline visitor check-in processes, enhance security, and improve overall visitor experience. Here are some common features you can expect from a VMS:
1. Visitor Registration
• Online pre-registration: Visitors can save time by entering their details online through the visitor registration system before arriving, reducing wait times during check-in.
• Information capture: Captures essential information such as the purpose of the visit, company affiliation, and any special requirements to personalize the visitor experience.
• Data accuracy: Ensures accurate visitor data entry, minimizing errors and enhancing security during registration.
2. Visitor Check-in/Check-out
• Self-service kiosks: Enables visitors to check in and out independently, freeing up receptionists’ time and reducing queues at entry points.
• Mobile check-in: Allows visitors to check in using their smartphones via a dedicated app, offering convenience and flexibility.
• Real-time tracking: Provides real-time updates on visitor arrivals and departures, aiding in resource allocation and planning.
3. ID Verification
• Secure access: Verifies visitor identities using government-issued IDs or biometric authentication, ensuring only authorized individuals enter the premises.
• QR code scanning: Streamlines the verification process by scanning QR codes on visitor passes or mobile devices, enhancing efficiency and security.
4. Access Control Integration
• Customized access levels: Integrates with access control systems to assign specific access permissions based on visitor categories (e.g., employees, contractors, guests).
• Time-based access: Restricts visitor access to designated areas during specified time frames, enhancing security and compliance with access policies.
5. Badge Printing
• Customizable badges: Generates visitor badges with customizable fields such as name, photo, company logo, and access restrictions for easy identification.
• Visitor tracking: Facilitates visual identification of authorized visitors and helps security personnel monitor visitor movements within the premises.
6. Host Notifications
• Instant alerts: Notifies hosts immediately upon visitor check-in, providing details such as visitor name, purpose of visit, and expected duration, ensuring a warm welcome and efficient hosting.
• Communication tools: Offers communication channels (email, SMS, app notifications) for hosts to coordinate with visitors, schedule meetings, or provide additional instructions.
7. Blacklist Screening
• Risk mitigation: Conduct background checks against blacklist databases to identify potential threats or individuals with restricted access, preventing security breaches and unauthorized entry.
• Real-time alerts: Alerts security personnel and hosts when a flagged visitor attempts to check in, triggering appropriate actions based on predefined protocols.
8. Data Privacy Compliance
• Secure storage: Stores visitor information in encrypted databases with restricted access, ensuring compliance with data protection regulations (e.g., GDPR, CCPA).
• Consent Management: Obtains visitor consent for data processing and sharing, providing transparency and control over personal information usage.
9. Reporting and Analytics
• Performance metrics: Generates detailed reports on visitor traffic, peak visitation hours, popular entry points, and visitor demographics, aiding in strategic decision-making and resource optimization.
• Trend analysis: Analyzes visitor behavior patterns over time to identify trends, opportunities for improvement, and areas of concern (e.g., unusual visitor activity).
10. Emergency Management
• Emergency alerts: Sends real-time alerts during emergencies (e.g., fire, evacuation) to visitors and staff, providing evacuation instructions and ensuring safety protocols are followed.
• Access control lockdown: Enables rapid lockdown of access points in emergencies, preventing unauthorized entry and controlling the flow of people for safety reasons.
11. Visitor Pre-Registration
• Streamlined check-in: Allows hosts to pre-register visitors before their arrival, expediting the check-in process and reducing wait times at reception.
• Enhanced planning: Enables hosts to plan for visitor arrivals, allocate resources effectively, and provide personalized services based on pre-registration information.
12. Visitor Watchlist
• VIP treatment: Flags VIP guests or high-priority visitors on the watchlist, ensuring they receive special attention, personalized services, and a memorable experience.
• Risk mitigation: Monitors flagged individuals closely, implements enhanced security measures, and notifies designated personnel in case of any suspicious activity or concerns
Types Of Modern Visitor Management System
Modern Visitor Management Systems (VMS) come in various types, each tailored to meet specific business needs and operational requirements. Here are some common types of modern VMS:
Cloud-Based Visitor Management Systems
• Accessible from anywhere: Allows users to manage visitor data, check-ins, and reports via a web-based interface, offering flexibility and convenience.
• Scalable: Easily scales with growing business needs without the need for additional hardware or infrastructure investments.
• Real-time updates: Provides real-time updates and notifications on visitor arrivals, check-ins, and security alerts.
Mobile Visitor Management Apps
•On-the-go management: Enables users to manage visitor registrations, check-ins, and access permissions using mobile devices such as smartphones and tablets.
•QR code scanning: Allows visitors to check in using QR codes generated on their mobile devices, reducing manual data entry and improving efficiency.
•Integration with other systems: Integrates seamlessly with access control systems, communication tools, and CRM software for enhanced functionality and data synchronization.
Self-Service Kiosk Visitor Management Systems
• Automated check-ins: Provides self-service kiosks at entry points for visitors to check in independently, reducing wait times and enhancing efficiency.
• Visitor badge printing: Generates visitor badges with relevant information such as name, photo, and access permissions for easy identification.
Customizable interfaces: Offers customizable kiosk interfaces to align with branding guidelines and provide a seamless user experience.
Integrated Visitor Management Systems
• Comprehensive solution: Integrates visitor management functionalities with other business systems such as access control, CCTV surveillance, and CRM platforms.
• Data synchronization: Ensures data consistency and accuracy across integrated systems, reducing duplicate entries and manual errors.
• Centralized control: Provides a centralized dashboard for administrators to monitor and manage visitor activities, security incidents, and compliance requirements.
On-premise Visitor Management Systems
• Local deployment: Installs VMS software on-site within the organization’s premises, offering full control over data privacy and security.
• Customizable configurations: Allows customization of features, workflows, and access controls to meet specific business policies and regulatory requirements.
• Offline functionality: Operates independently of internet connectivity, ensuring continuity of visitor management processes during network disruptions.
Visitor Management Systems with Facial Recognition
• Biometric authentication: Utilizes facial recognition technology for fast and secure visitor authentication during check-ins.
• Enhanced security: Verifies visitor identities with high accuracy, reducing the risk of unauthorized access and identity fraud.
• Privacy considerations: Adheres to data privacy regulations and guidelines for biometric data collection, storage, and processing.
Addressing Specialized Visitor Management Needs
Modern workplaces require more than just basic check-in tools. As businesses evolve, so do the demands around visitor security, automation, compliance, and flexibility. That’s why the next generation of Visitor Management Systems (VMS) are built to handle specific operational and industry-level challenges.
Here are key VMS configurations that address different needs—especially in enterprise, high-security, and regulated environments.
Biometric Visitor Management System
Biometric technology is transforming workplace security. A biometric visitor management system uses facial recognition or fingerprint scanning to authenticate visitors with a high level of accuracy.
Benefits include:
- Faster repeat visitor authentication
- Secure check-ins without badges or cards
- Prevention of impersonation or unauthorized entry
- Full alignment with identity verification policies
Biometric VMS is ideal for environments like R&D labs, government offices, data centers, and corporate HQs that require tight access control.
Integrated Visitor Management System
An integrated visitor management system connects seamlessly with your existing IT ecosystem—HR databases, access control systems, CRM tools, and surveillance systems.
Advantages:
- Unified visitor and employee data records
- Automated workflows and meeting scheduling
- Real-time synchronization across systems
- Custom access rules based on user role or visitor type
This type of VMS improves operational cohesion and supports enterprise-level governance and compliance standards.
Visitor Management Kiosks and Self-Registration
Self-service is now a standard expectation in modern offices. Visitor management kiosks support high-traffic locations while reducing bottlenecks at the front desk.
Use cases and features:
- Touchless, tablet-based check-in
- On-demand badge printing
- Self-scanning for QR codes or pre-registered IDs
- Custom interfaces aligned with your brand
Whether in coworking spaces, universities, or event venues, kiosks offer an efficient and user-friendly first impression.
Enterprise Office Visitor Management
Managing thousands of visitors across multiple locations requires centralized control and deep flexibility. A dedicated enterprise office visitor management system includes:
- Multi-location visitor logs and analytics
- Central policy enforcement with location-level overrides
- VIP workflows and white-label customization
- Admin dashboards for audit and compliance tracking
Enterprise-level VMS platforms like Vizitor are built to scale with your organization—whether you have five locations or fifty.
Visitor Authentication and Process Compliance
In regulated sectors such as healthcare, finance, legal, and logistics, compliance is non-negotiable. A visitor authentication and management system supports this by:
- Capturing government-issued ID or biometric data at check-in
- Restricting access based on zones, time, or visitor profile
- Storing visitor data in encrypted formats for audit-readiness
- Logging visit times, host interactions, and exit times
This ensures that every visitor interaction is both traceable and policy-compliant.
Top Business Benefits of Using a Visitor Management System
A modern visitor management system offers much more than digital check-ins—it directly supports your business operations, brand image, and security. Here’s how:
1. Enhanced Brand Perception
Digital check-in systems show visitors that your business is professional, secure, and tech-forward—leaving a strong first impression.
2. Time and Resource Efficiency
By automating check-ins, badge printing, and notifications, you reduce reception workload and improve throughput at entry points.
3. Reduced Risk & Liability
VMS systems log visitor data, access points, and timestamps—critical for audits, safety protocols, and emergency response.
4. Centralized Compliance Management
Easily demonstrate adherence to regulatory frameworks (like GDPR, HIPAA, ISO) with built-in audit trails and data retention controls.
5. Smart Data Insights for Business Decisions
Use visitor data to optimize staffing, scheduling, and space planning—especially in multi-location or hybrid workplaces.
6. Seamless Hybrid & Multi-Tenant Experience
For coworking spaces and large office parks, VMS enables secure, branded check-ins with centralized visibility across multiple tenants.
Whether you’re a small startup or an enterprise, a smart VMS can be the foundation for safer, more streamlined workplace operations.
Frequently Asked Questions (FAQs)
What are the key benefits of a visitor management system?
A visitor management system improves security, enhances guest experience, streamlines check-in, and ensures regulatory compliance. It reduces manual effort and helps make your business more professional.
Why is visitor management important in an office environment?
Visitor management is crucial for protecting staff, data, and facilities. It prevents unauthorized access, ensures clear visitor tracking, and improves front-desk efficiency.
How does a VMS improve data privacy and compliance?
Modern VMS platforms store visitor information securely with encryption, audit trails, and access controls, helping you comply with regulations like GDPR, HIPAA, and CCPA.
Can a visitor management system be customized for different industries?
Yes. Systems like Vizitor allow custom workflows, branding, visitor types (e.g., contractors, vendors), and integrations—ideal for corporate, healthcare, education, and government sectors.
Does a visitor management system support touchless or mobile check-in?
Absolutely. Most modern VMS tools offer QR code, facial recognition, or mobile app check-ins for safe, fast, and contactless entry.
Wrapping It Up
In conclusion, Vizitor is unparalleled in its provision of the best Visitor Management System (VMS) solutions. Leveraging cutting-edge technology like cloud-based systems, mobile apps, and facial recognition, Vizitor offers advanced security measures and streamlined visitor management processes. Its user-friendly interfaces, whether through self-service kiosks, mobile apps, or web-based portals, ensure ease of use for both visitors and administrators, resulting in efficient operations.
Moreover, Vizitor understands the unique needs of businesses, offering customizable solutions that can be tailored to specific requirements, including branding, access controls, and integration with existing systems. Compliance with regulations and robust data privacy and security measures are top priorities for Vizitor, ensuring secure data storage, encryption, and access control.
The reporting and analytics capabilities of Vizitor provide real-time insights into visitor traffic, trends, and key metrics, empowering businesses to make informed decisions and optimize resource allocation.
Additionally, Vizitor’s dedicated support team ensures a smooth implementation process and ongoing assistance, making it the preferred choice for organizations looking to enhance operations and create a safe and welcoming environment for their visitors.










